-
Products and Features
- Getting Started with CloudRaya Container Registry
- How to use Sudo on a CloudRaya Linux VM
- Keeping Your CloudRaya Linux VMs Up-to-Date
- Maximizing StorageRaya with Essential Practices
- Assign Multiple IP Addresses to Virtual Machine
- Generating a CloudRaya API key
- Simplify CloudRaya Management with API
- Deploying a Virtual Machine on CloudRaya
- Deploying a Kubernetes Cluster on KubeRaya
- Using StorageRaya – CloudRaya S3 Object Storage
- Opening Ping Access on Cloud Raya VM Public IP
- Maximize Your Storage Raya Access Speed with Content Delivery Network (CDN)
- How to Create Project Tag in Cloud Raya for More Organized VM Billing Report
- Exporting Cloud Raya VM to outer Cloud Raya's Infrastructure using Acronis Cyber Protect
- SSO Management on Cloud Raya
- Using the SSH key Feature in Cloud Raya Dashboard
- Cloud Raya Load Balancer, Solution to Distribute Load Equally
- Create your own VPN server with DNS-Level AdBlocker using PiVPN
- Fix Broken LetsEncrypt SSL Certificate due to Expired Root CA Certificate
- How to Make a Snapshot and Configure VM Backup in Cloud Raya
- How to Request Services or Licenses Products
- Adding, Attaching, and Resize Root Storage Disk in Cloud Raya VPS
- Managing your DNS Zone with DNS Bucket in Cloud Raya
- Create VM, Custom Package, Reinstall VM, and Adjusting Security Profile
- How to backup Linux VM via Acronis in Cloud Raya
- How to Backup Desktop Linux and Windows via Acronis in Cloud Raya
- Backing-Up Cloud Raya Windows VM Using Acronis Cyber Protect
- Load Balancing in Cloud Raya
- Establishing a VPN in Cloud Raya
- Generating an API Token
- Deploying a Virtual Machine in Cloud Raya
- Show Remaining Articles16 Collapse Articles
-
- How to backup Linux VM via Acronis in Cloud Raya
- How to Backup Desktop Linux and Windows via Acronis in Cloud Raya
-
- Maximizing StorageRaya with Essential Practices
- Using StorageRaya – CloudRaya S3 Object Storage
- Building a Static Website Using Storage Raya S3 Bucket
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Maximize Your Storage Raya Access Speed with Content Delivery Network (CDN)
- Managing Storage Raya from various tools and from various OS
- Binding NextCloud with CloudRaya S3 Object Storage as External Storage Mount
-
- How to use Sudo on a CloudRaya Linux VM
- Keeping Your CloudRaya Linux VMs Up-to-Date
- Implement Multi-Factor Authentication on CloudRaya Linux VM
- Assign Multiple IP Addresses to Virtual Machine
- Deploying a Virtual Machine on CloudRaya
- Configurating cPanel Using Ubuntu 20.04 on CloudRaya – Part 2
- Deploying cPanel Using Ubuntu 20.04 on CloudRaya - Part 1
- Exporting Cloud Raya VM to outer Cloud Raya's Infrastructure using Acronis Cyber Protect
- Using the SSH key Feature in Cloud Raya Dashboard
- Adding, Attaching, and Resize Root Storage Disk in Cloud Raya VPS
- Create VM, Custom Package, Reinstall VM, and Adjusting Security Profile
- How to backup Linux VM via Acronis in Cloud Raya
- Backing-Up Cloud Raya Windows VM Using Acronis Cyber Protect
- Deploying a Virtual Machine in Cloud Raya
-
Integration
- Implement Multi-Factor Authentication on CloudRaya Linux VM
- Accessing KubeRaya Cluster Using the Kubernetes Dashboard
- Building a Static Website Using Storage Raya S3 Bucket
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Integrating Strapi Content to Frontend React - Part 3
- Content Management with Strapi Headless CMS - Part 2
- Strapi Headless CMS Installation in CloudRaya - Part. 1
- Using SSH Key on CloudRaya VM with PuTTY
- Installing Multiple PHP Versions in One VM for More Flexible Web Development
- Replatforming Apps to K8s with RKE and GitLab CI
- OpenAI API Integration: Completions in PHP
- Building an Email Server on CloudRaya Using iRedMail
- Improving Email Delivery with Sendinblue SMTP Relay
- Building a Self Hosted Password Manager Using Passbolt
- How to Install Podman on Almalinux/Rocky Linux 9
- ElkarBackup: GUI Based backup Tools based on Rsync and Rsnapshot
- Improving Webserver Performance with SSL Termination on NGINX Load Balancer
- Using NGINX as an HTTP Load Balancer
- Automating Task with Cronjob
- Upgrade Zimbra and the OS Version
- Deploy Mailu on Rancher Kubernetes
- Export and Import Database in MySQL or MariaDB Using Mysqldump
- Backup & Sync Local and Remote Directories Using RSYNC
- Managing Storage Raya from various tools and from various OS
- Binding NextCloud with CloudRaya S3 Object Storage as External Storage Mount
- Simple monitoring and alerting with Monit on Ubuntu 22.04 LTS
- VS Code on your browser! How to install code-server on a VM
- Implementing Redis HA and Auto-Failover on Cloud Raya
- Using XFCE Desktop Environment on Cloud Raya VM
- Installing Python 3.7-3.9 on Ubuntu 22.04 Jammy LTS using PPA
- Implementing Continuous Integration with Gitlab CI and Continuous Delivery with Rancher Fleet
- Using Collabora Online on Cloud Raya NextCloud's VM
- Installing NextCloud in Cloud Raya- Detail Steps from the Beginning to the Very End
- Set Up High Availability PostgreSQL Cluster Using Patroni on Cloud Raya
- Set Up WAF KEMP in Cloud Raya Part 2
- Set Up WAF KEMP in Cloud Raya Part 1
- Using the SSH key Feature in Cloud Raya Dashboard
- Monitor Your Services Uptime Using Uptime Kuma
- Hosting Static Website with Hugo on Cloud Raya
- Kubernetes Ingress Controller using SSL in CloudRaya
- Reverse Proxy management using Nginx Proxy Manager
- Create your own VPN server with DNS-Level AdBlocker using PiVPN
- How to deploy Portainer on Linux to easily manage your docker containers
- High Availability Kubernetes Using RKE in Cloud Raya Part 3
- High Availability Kubernetes Using RKE in Cloud Raya Part 2
- High Availability Kubernetes Using RKE in Cloud Raya Part 1
- How to backup Linux VM via Acronis in Cloud Raya
- How to Backup Desktop Linux and Windows via Acronis in Cloud Raya
- Deploying Magento on Cloud Raya
- How to Install Nextcloud on Cloud Raya
- How to Install CWP in Cloud Raya
- How to Install Node.js and Launch Your First Node App
- How to install and secure MariaDB on Ubuntu 18.04 and 20.04 on Cloud Raya
- How to Install and Securing MongoDB on Ubuntu 18.04 and 20.04
- Classes: Post Installation on Ansible
- Classes: Install and Configure Ansible
- Classes: Introduction to Ansible for a robust Configuration Management
- How to Setup Active Directory Domain Service & DNS with Cloud Raya
- How to Host Your Own Docker Hub in Cloud Raya
- How to Setup Your Own Laravel with Nginx in Ubuntu 18.04
- How to Deploy Container in Cloud Raya using Docker
- Securing CentOS with iptables
- Install and Configure Squid Proxy in Ubuntu
- Installing Apache and Tomcat: A Quick Way
- Securing Ubuntu with UFW
- Install a Node.js and Launch a Node App on Ubuntu 18.04
- Installing LAMP in Ubuntu
- Installing LEMP Stack on Ubuntu 18.04
- Show Remaining Articles53 Collapse Articles
-
- Articles coming soon
-
- Implement Multi-Factor Authentication on CloudRaya Linux VM
- Configurating cPanel Using Ubuntu 20.04 on CloudRaya – Part 2
- Deploying cPanel Using Ubuntu 20.04 on CloudRaya - Part 1
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Integrating Strapi Content to Frontend React - Part 3
- Content Management with Strapi Headless CMS - Part 2
- Strapi Headless CMS Installation in CloudRaya - Part. 1
- Using SSH Key on CloudRaya VM with PuTTY
- Building an Email Server on CloudRaya Using iRedMail
- Improving Email Delivery with Sendinblue SMTP Relay
- Building a Self Hosted Password Manager Using Passbolt
- ElkarBackup: GUI Based backup Tools based on Rsync and Rsnapshot
- Improving Webserver Performance with SSL Termination on NGINX Load Balancer
- Using NGINX as an HTTP Load Balancer
- Upgrade Zimbra and the OS Version
- Deploy Mailu on Rancher Kubernetes
- Managing Storage Raya from various tools and from various OS
- Binding NextCloud with CloudRaya S3 Object Storage as External Storage Mount
- Simple monitoring and alerting with Monit on Ubuntu 22.04 LTS
- VS Code on your browser! How to install code-server on a VM
- Implementing Redis HA and Auto-Failover on Cloud Raya
- Using XFCE Desktop Environment on Cloud Raya VM
- Implementing Continuous Integration with Gitlab CI and Continuous Delivery with Rancher Fleet
- Using Collabora Online on Cloud Raya NextCloud's VM
- Installing NextCloud in Cloud Raya- Detail Steps from the Beginning to the Very End
- Set Up WAF KEMP in Cloud Raya Part 2
- Set Up WAF KEMP in Cloud Raya Part 1
- Monitor Your Services Uptime Using Uptime Kuma
- Create your own VPN server with DNS-Level AdBlocker using PiVPN
- How to deploy Portainer on Linux to easily manage your docker containers
- High Availability Kubernetes Using RKE in Cloud Raya Part 3
- High Availability Kubernetes Using RKE in Cloud Raya Part 2
- High Availability Kubernetes Using RKE in Cloud Raya Part 1
- How to Install Nextcloud on Cloud Raya
- Classes: Post Installation on Ansible
- Classes: Install and Configure Ansible
- Classes: Introduction to Ansible for a robust Configuration Management
- Connect Windows Active Directory on Cloud Raya with Azure AD
- How to Host Your Own Docker Hub in Cloud Raya
- How to Deploy Container in Cloud Raya using Docker
- Show Remaining Articles25 Collapse Articles
-
- Accessing KubeRaya Cluster Using the Kubernetes Dashboard
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Integrating Strapi Content to Frontend React - Part 3
- Content Management with Strapi Headless CMS - Part 2
- Strapi Headless CMS Installation in CloudRaya - Part. 1
- Creating Interactive Chatbot with OpenAI API in PHP
- Installing Multiple PHP Versions in One VM for More Flexible Web Development
- OpenAI API Integration: Completions in PHP
- Improving Webserver Performance with SSL Termination on NGINX Load Balancer
- Using NGINX as an HTTP Load Balancer
- Automating Task with Cronjob
- How to Deploy Django App on Cloud Raya VM Using Gunicorn, Supervisor, and Nginx
- How to Install Node.js and Launch Your First Node App
- How to Setup Your Own Laravel with Nginx in Ubuntu 18.04
- Install a Node.js and Launch a Node App on Ubuntu 18.04
-
- How to use Sudo on a CloudRaya Linux VM
- Keeping Your CloudRaya Linux VMs Up-to-Date
- Implement Multi-Factor Authentication on CloudRaya Linux VM
- Using SSH Key on CloudRaya VM with PuTTY
- Building a Self Hosted Password Manager Using Passbolt
- Improving Webserver Performance with SSL Termination on NGINX Load Balancer
- Export and Import Database in MySQL or MariaDB Using Mysqldump
- Backup & Sync Local and Remote Directories Using RSYNC
- How to Deploy Django App on Cloud Raya VM Using Gunicorn, Supervisor, and Nginx
- Set Up WAF KEMP in Cloud Raya Part 2
- Set Up WAF KEMP in Cloud Raya Part 1
- Using the SSH key Feature in Cloud Raya Dashboard
- How to backup Linux VM via Acronis in Cloud Raya
- How to Backup Desktop Linux and Windows via Acronis in Cloud Raya
- Securing CentOS with iptables
- Securing Ubuntu with UFW
- Show Remaining Articles1 Collapse Articles
-
- Configurating cPanel Using Ubuntu 20.04 on CloudRaya – Part 2
- Deploying cPanel Using Ubuntu 20.04 on CloudRaya - Part 1
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Integrating Strapi Content to Frontend React - Part 3
- Content Management with Strapi Headless CMS - Part 2
- Strapi Headless CMS Installation in CloudRaya - Part. 1
- Creating Interactive Chatbot with OpenAI API in PHP
- Installing Multiple PHP Versions in One VM for More Flexible Web Development
- Building an Email Server on CloudRaya Using iRedMail
- Building a Self Hosted Password Manager Using Passbolt
- Improving Webserver Performance with SSL Termination on NGINX Load Balancer
- Using NGINX as an HTTP Load Balancer
- Installing Python 3.7-3.9 on Ubuntu 22.04 Jammy LTS using PPA
- Reverse Proxy management using Nginx Proxy Manager
- Install and Configure Squid Proxy in Ubuntu
- Installing Apache and Tomcat: A Quick Way
- Installing LAMP in Ubuntu
- Installing LEMP Stack on Ubuntu 18.04
- Show Remaining Articles3 Collapse Articles
-
- Building a Static Website Using Storage Raya S3 Bucket
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Integrating Strapi Content to Frontend React - Part 3
- Content Management with Strapi Headless CMS - Part 2
- Strapi Headless CMS Installation in CloudRaya - Part. 1
- Creating Interactive Chatbot with OpenAI API in PHP
- Installing Multiple PHP Versions in One VM for More Flexible Web Development
- OpenAI API Integration: Completions in PHP
- Hosting Static Website with Hugo on Cloud Raya
- Deploying Magento on Cloud Raya
- How to Install CWP in Cloud Raya
- How to Setup Active Directory Domain Service & DNS with Cloud Raya
-
- Articles coming soon
Connect Windows Active Directory on Cloud Raya with Azure AD
Many organizations running in today’s enterprises are not simply migrating 100% of all user/group object data into the cloud. They’re still wanting to maintain some presence of Active Directory Domain Services (i.e. AD DS on-prem) so they can still support authentication to other on-prem based applications and services. This means you need to synchronize identities between Azure AD and Windows Active Directory. Azure AD Connect is the Microsoft solution that will get you there.
Azure AD Connect supports many topologies, including a single Active Directory, multiple Active Directories, and even multiple Office 365 tenants.
In this guide, we’re not going to cover every option for installation of Azure AD Connect. This is because there’s a variety of ways to configure it. But we will explain one of the easiest ways to do so.
Prepare the environment for Azure AD Connect
Before setting up the Azure AD connect, there are three major prerequisites that we need to setup:
- You need an Azure AD tenant. You get one with an Azure free trial.
- Setup your on-premises Active Directory Domain Controller VM in Cloudraya, the one which will connect with the Azure AD
- Have on-premises Active Directory schemas
For the complete Prerequisites, check out Official Azure AD Connect: Prerequisites from Microsoft Documentation
Setup a Windows VM in Cloudraya
First, we need to create a Windows VM in Cloudraya. Navigate to your Cloudraya Admin Panel and Add New VM. Make sure the VM is having this following specification so it can meet the minimum specification for Azure AD Connect:
- 2 CPU Core
- 20 GB of Storage
- 2 GB of RAM
With these specifications, the best VM package to pick is small-c2
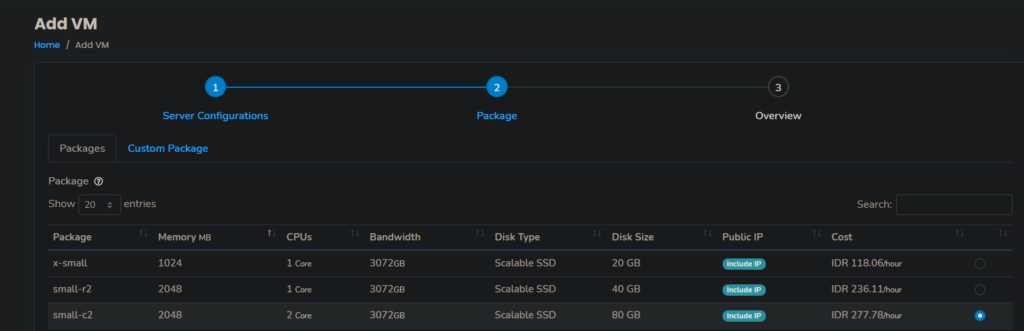
Also, don’t forget to set the Cloudraya Security Profile to allow RDP Port (default port: 3389)
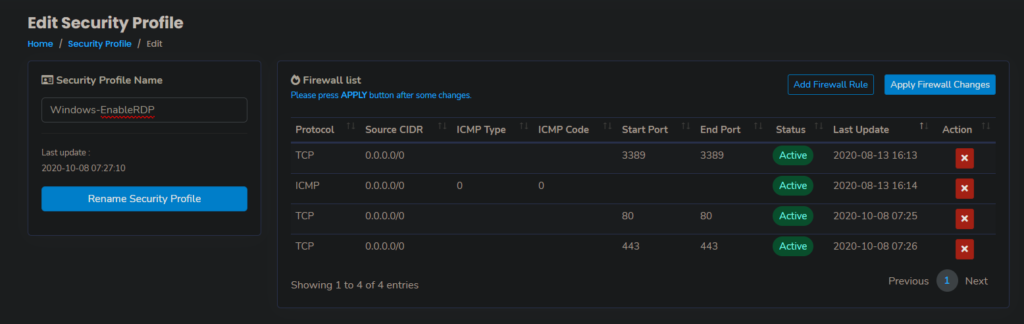
After the VM has been created successfully, continue to access the VM via RDP
Setup the on-premises Active Directory and Active Directory Domain Controller
Before connecting our own Active Directory with Azure AD, we need to install an Active Directory Domain Controller role. It will act as Azure AD Connector.
Open Server Manager and click on Manage -> Add Roles and Features. On the Select Server Roles tab, check the Active Directory Domain Services button
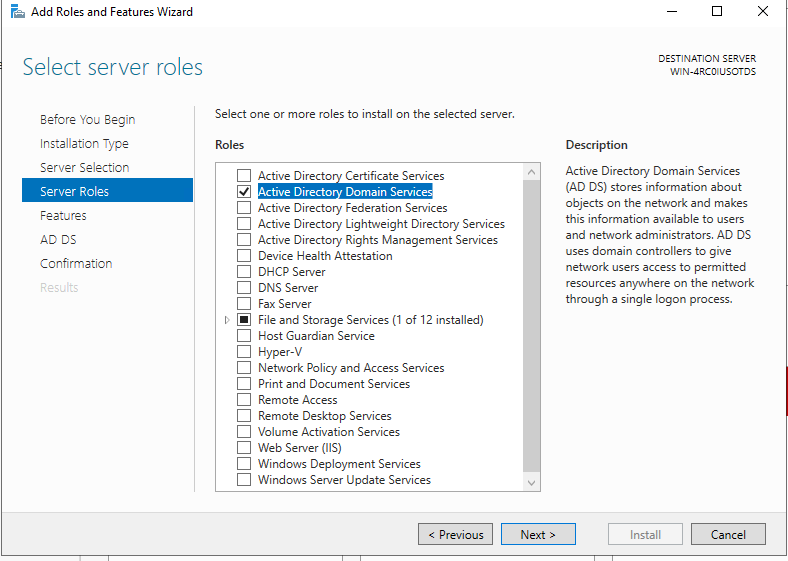
Continue the configuration until the role has been installed successfully.
The next step is promoting the VM as an Active Directory Domain Controller. You can find the full steps on How to setup Active Directory Domain Service with Cloud Raya.
One thing you need to make sure is when configuring the domain name. For the sake of simplicity, you need to use Valid FQDN (Fully-Qualified Domain Name) and Valid TLD. For example, use .com, .net, .org and so on instead of .local, .staging and so forth.
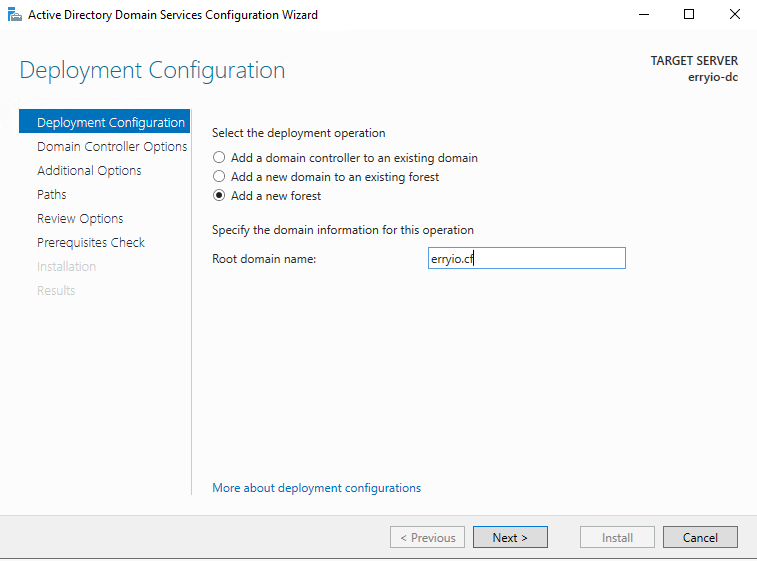
After the VM has been promoted as a Domain Controller, your on-premises Active Directory is now ready to be connected with the Azure AD. Then, the next step is to prepare the Azure AD environment.
Setup Azure AD Environment
First, you need to have an Azure Account. As stated in the beginning of this article, you can get this account with free trial provided by Microsoft.
If you already have a working Azure account, open the Azure Portal. Then, navigate to the Azure Active Directory dashboard by searching it on the portal.
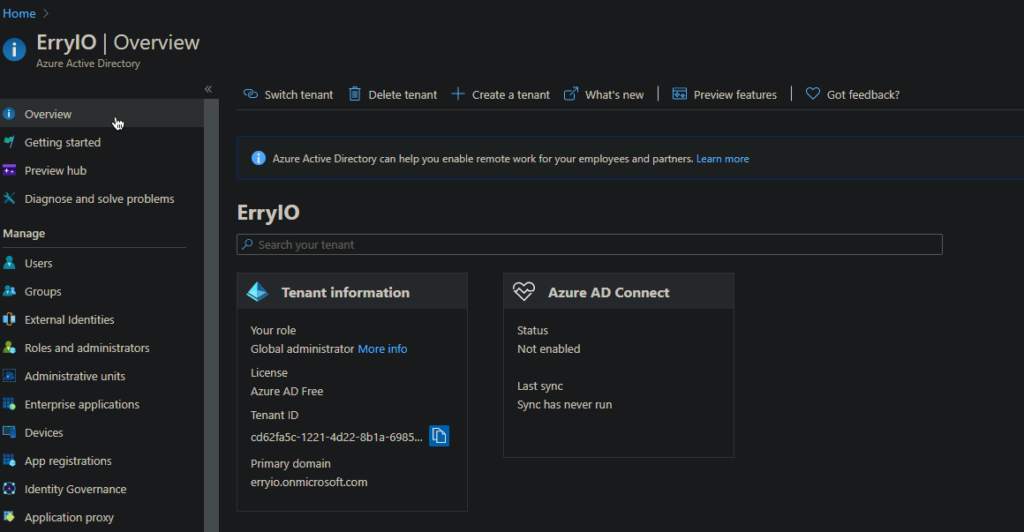
To connect to Azure AD with your on-premises active directory credentials, you need to add the matching domain on the Azure AD. This is why you need to use the Valid FQDN and Valid TLD on your on-premises AD. To do this, navigate to Custom Domain Blade and click on Add Custom Domain
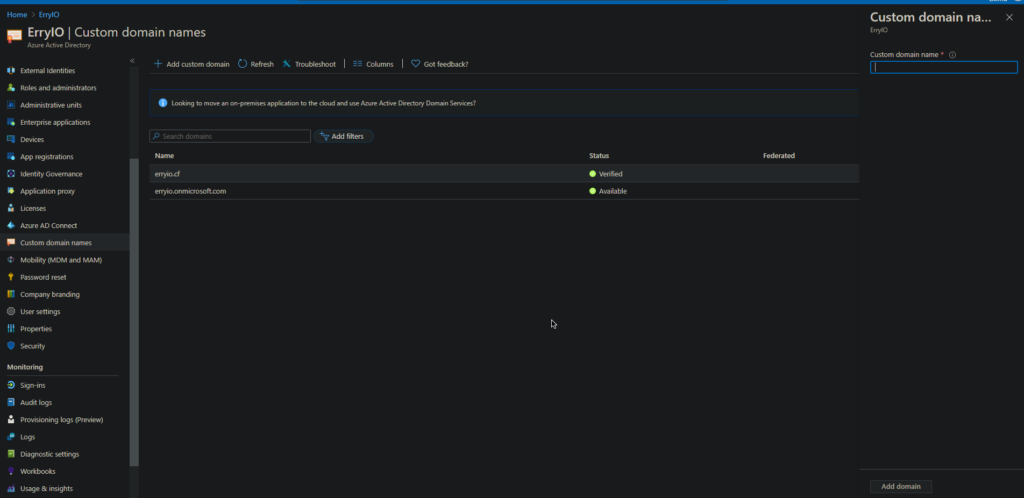
You also need the domain to be verified. After adding the custom domain name, Azure will ask you to add a new TXT DNS record on your domain. Thus, add the record on your Domain Name DNS management tool.
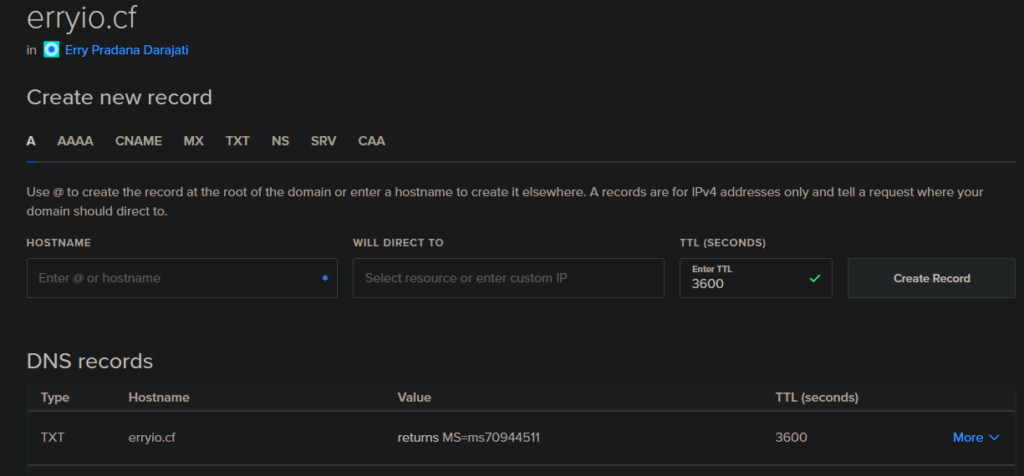
When the domain has been validated, your custom domain will be shown as Verified on the Custom Domain Name dashboard.
Install and Configure Azure AD Connect
Now the on-premises AD and Azure AD end has been configured. The next thing to do is to configure the Azure AD connect.
Download Azure AD Connect
Firstly, download Azure AD Connect application. The easiest way to download the app is by navigating to the Azure Active Directory dashboard. Then, click on the Azure AD Connect blade. You will see a link that leads to Azure AD Connect download page
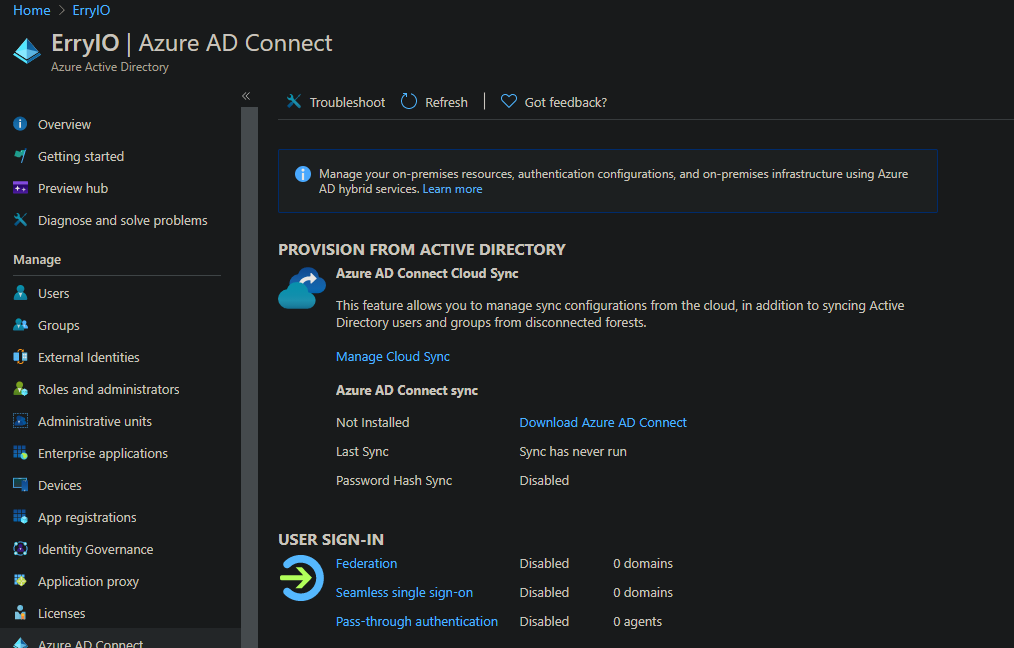
Setup and Configuration
After the download has completed, we can continue with the Azure AD Connect setup and configuration. To do so, open the downloaded file and install.
After the installation, there will be new application on your desktop named “Azure AD Connect”, open the application.
When we get into the installation method options of Azure AD Connect, we have two options:
- Express Settings
- Custom Installation
You may want to pick Express settings if your on-premises AD is using single-forest topology and are using Password Hash Synchronization for the authentication option. Otherwise, you may click on the Custom Installation. In this guide, we will pick a Customize option
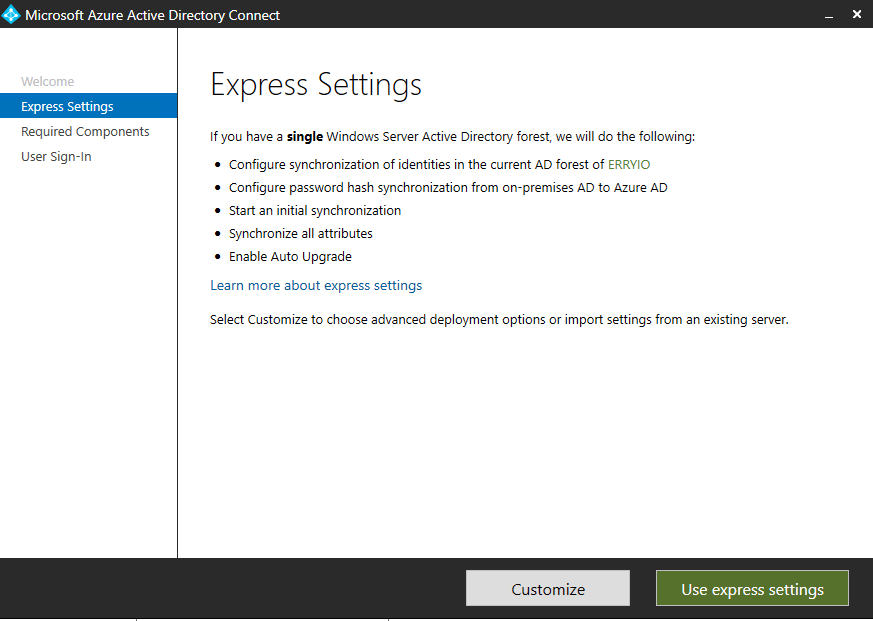
Upon clicking Customize button, installation wizard does a quick check to ensure no other synchronization services are running. Then, you can then specify any existing SQL Servers, service accounts, or synchronization groups.
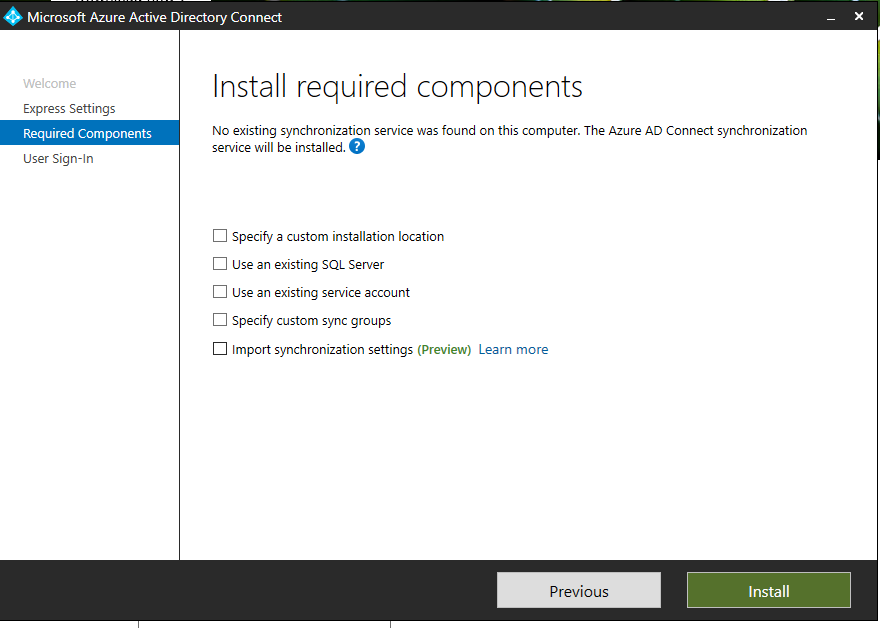
Authentication
After you specify the required components and/or custom installation location, the wizard will continue with the authentication method selection.
Accordingly, there are three ways of authentication method to sign in:
- Password Hash Synchronization
- Pass-through authentication
- Federated authentication (using ADFS or Third-party applications)
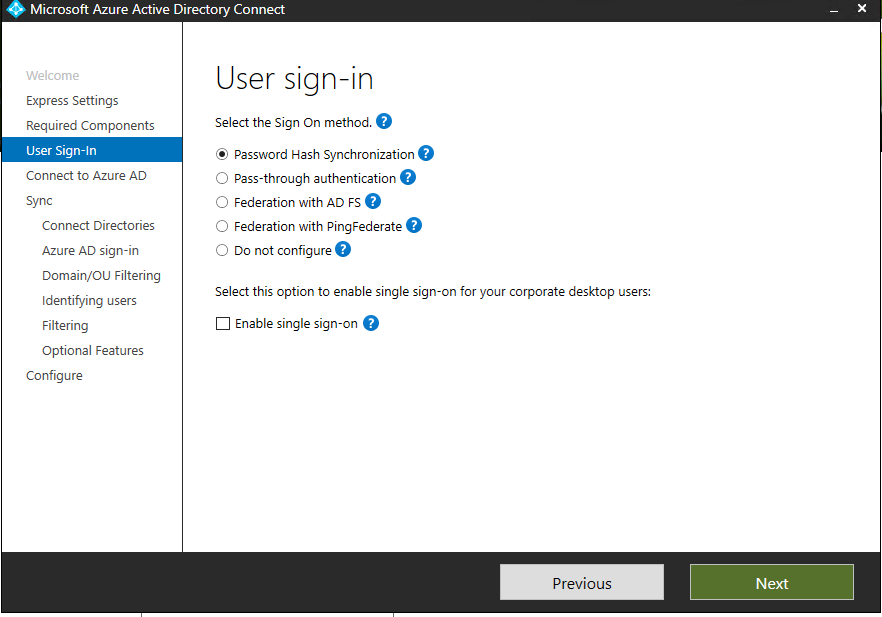
Password hash synchronization (PHS) – Password Hash Sync enables users to use the same username and password that they use on-premises. You don’t have to deploy any additional infrastructure besides Azure AD Connect.
Pass-through authentication (PTA) – This option is similar to password hash sync. However, it also provides a simple password validation using on-premises software agents for organizations with strong security and compliance policies.
Federated authentication – When you choose this authentication method, Azure AD will hand off the authentication process. This is to a separate trusted authentication system, such as AD FS or a third-party federation system, to validate the user’s sign-in. For simplicity sake, you can use PHS for the rest of this installation
Connect to Azure AD
We are now ready to connect to Azure AD, we need an account with Global Administrator account. If you’re using Federation with ADFS, don’t use an account on the same domain you plan to enable for federation. A good way around this is to create that global admin account on the .onmicrosoft.com domain to facilitate this.
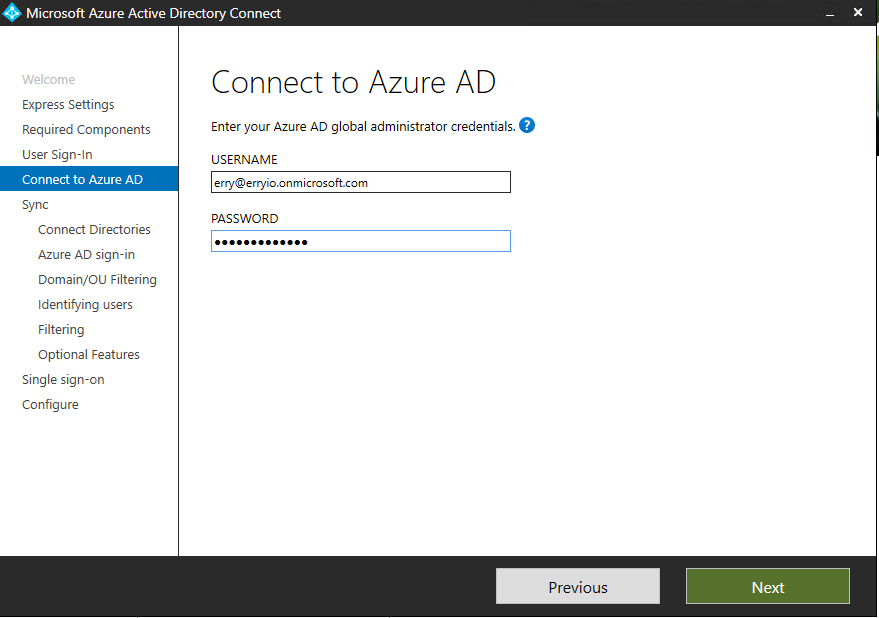
If you are entering a correct account, we can continue to integrate the on-premises forest first. Due to this, you need an Enterprise Admin account on the On-premises forest.
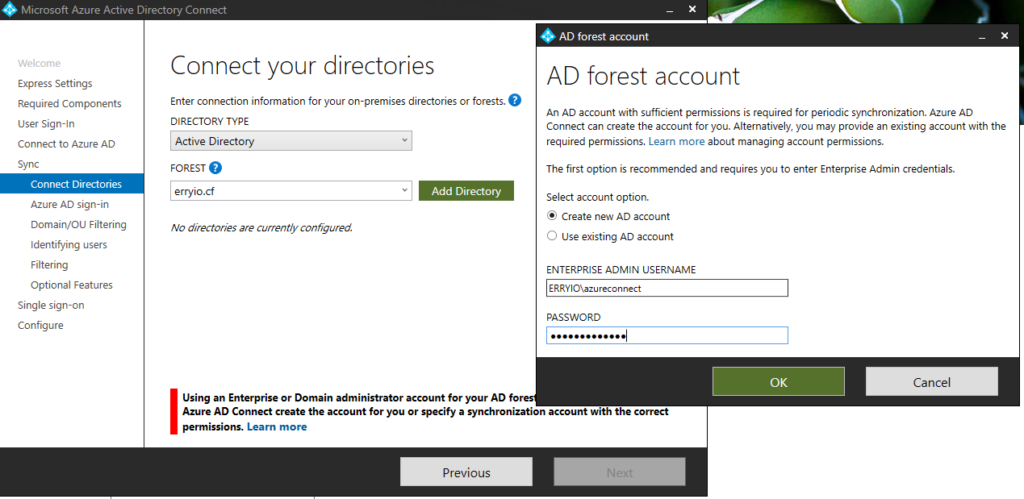
Now as you can see above, you can create a new account or use an existing account. If you opt to create a new account, you need to provide the enterprise admin credentials. This is to allow the wizard to provision a new account in Active Directory Directory Services with the appropriate permissions.
If you specify an existing account, specify the FQDN or NETBIOS name of the account (i.e. contoso.com\administrator or CONTOSO\Administrator). One thing to note about using an existing account is that it only needs default read permissions. However, some scenarios may require additional permissions. For those details, you can read the Azure AD Connect Accounts and Permissions for more information.
Verification and Synchronization
This next phase is about verification of the domains we’ve just connected. UserPrincipalName (or UPN) in Active Directory is the attribute users use to sign into Azure AD, Office 365, etc. Therefore, the domain (or UPN-suffix) should be verified before we synchronize any objects into Azure AD.
If you’re using Pass Through Authentication, you need to have at least one verified domain. This is in order to proceed through the remaining steps in the installation wizard. That is why we need to do the Custom Domain Verification on the beginning of this guide
By default, Synchronize everything from the On-premises AD is the behavior upon getting to the next phase of the wizard. In Domain and Organizational Unit (OU) filtering, we can specify what we DO NOT want to synchronize to Azure AD.
This step is pretty straightforward. That being said, you might have conconcerns about which domains and or OUs you don’t want to synchronize. If so, you may review the domain-based filtering and OU-based filtering articles. You can easily find them on Microsoft’s doc library before you make any changes.
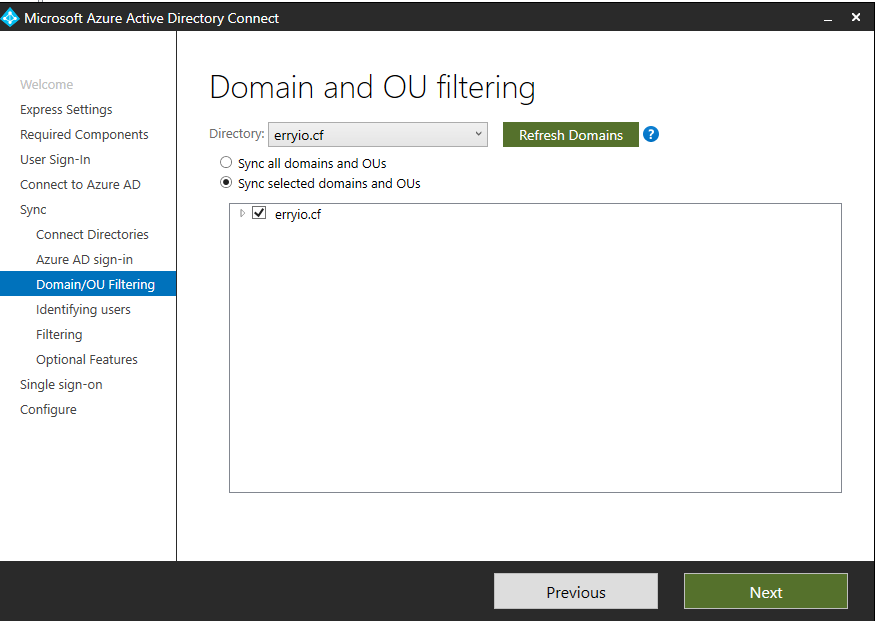
Identify Users
Next is how we identify users in Active Directory and how we want them represented in Azure AD. In some cases, you may have a user with multiple representations across multiple domains (i.e. an enterprise admin). You may also have the same thing for B2B, guest accounts, or mail enabled contacts in Active Directory.
Simply put, you need to uniquely identify your users to avoid duplicate entries in Azure AD. This step helps you define that and how you’d like to identify those users.
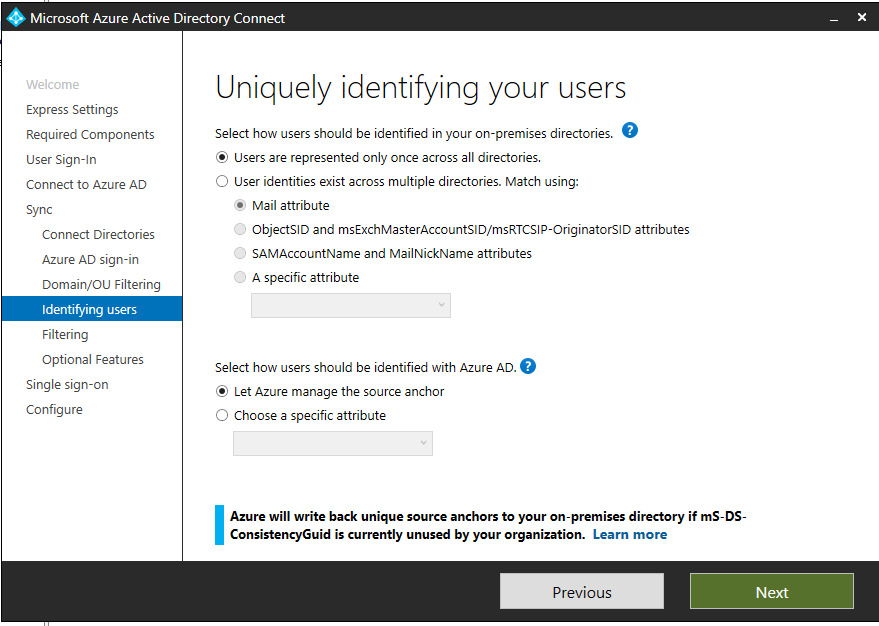
The options are pretty straight forward:
- Users are represented once across all forests – all users are individual objects in Azure AD.
- Mail attribute – This option will join users and contacts if their mail attribute has the same value in different forests. If you’ve used services like GALSync to create contacts, you’ll want to specify this option.
- ObjectSID and msExchangeMasterAccountSID/msRTCSIP-OriginatorSid – This option joins an enabled user in an account forest with a disabled user in a resource forest. In the Exchange realm of taxonomy, this is known simply as a linked mailbox. This option can also be leveraged if you only use Lync or Skype for Business and Exchange is not present in the forest.
- SAMAccountName and MailNickName – This leverages those attributes where its expected that the sign-in ID for the user can be found.
- Specific Attributes – You can select and define your own attribute. The only limitation here is this has been to be a searchable attribute across the Active Directory metaverse.
Filter Users and Devices
As we go into the next steps of this wizard, we need to look at the available filtering options. Some examples of this would be group-based filtering. This allows us to synchronize only a smaller subset of objects for a specific use. For example, pilot, proof of concept, test, etc.). Please note that this is only meant and intended for pilot type deployments instead of large scale production deployments.
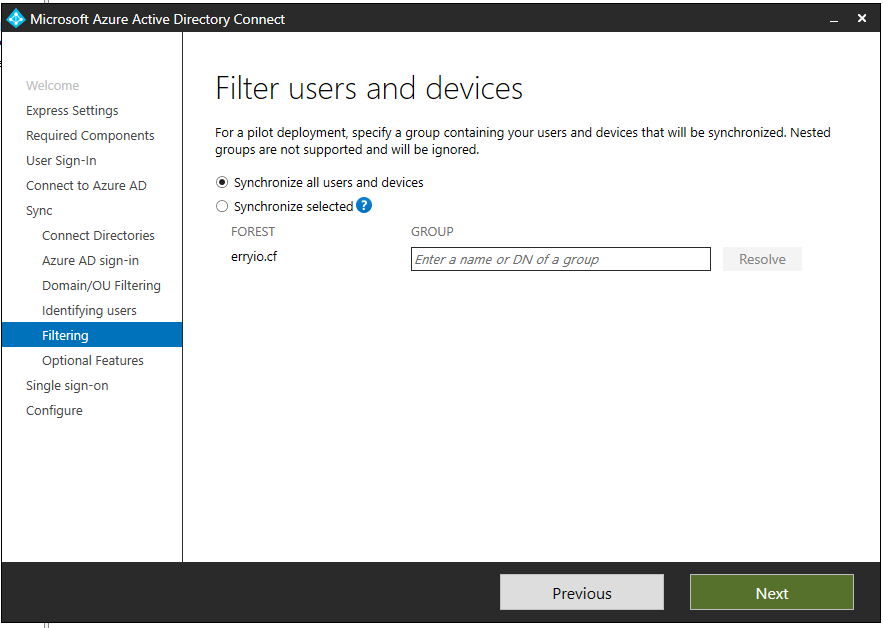
Optional Features
As we go into the next step of the wizard, we talk about the use of optional features. Here we can add options like Exchange hybrid deployment, Password writeback, Group writeback, etc. to the mix.
The list of features each has their own description if you click the source link above. If you go through the wizard, you’ll see the ? next to each item. This will also provide you with that description of each feature as well.
I won’t belabor the details of each feature in this blog. But if you want to add additional features, you can simply set that. Then, it will allow you to provision/enable that feature in the wizard directly as a next step.
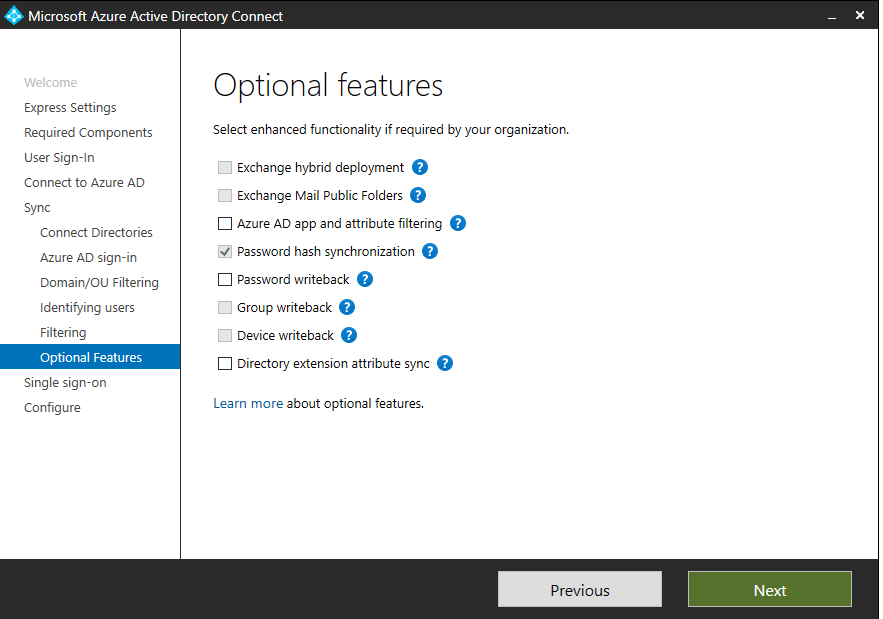
On this guide, we are not enabling anything beside the Password Hash Synchronization.
Regardless you’re using password synchronization or pass-through authentication, you simply need to ensure these two steps are completed:
- Create the necessary computer object account in your on-prem Active Directory
- Configure the intranet zone of the client machines to support SSO
Configure and Verify Everything
Once you hit the final steps in the wizard, you’ll simply need to configure and verify. You need to check whether you wish to start the synchronization process as soon as the wizard completes. Also, you can do this if you wish to enable Staging Mode. Accordingly, staging mode has some other steps. However, we will save them for another blog.
For now, we’ll synchronize (as we would if this were our first time running through the wizard) and proceed to the verification steps.
How would you know whether your Azure AD is connected to the On-premises AD? You can connect to the Azure AD Dashboard on the Azure portal.
After that, navigate to Users blade. If the synchronization has succeeded, you can find the users which on your on-premises being synchronized on the portal
Finally, it is ready!
At last, your on-premises directory is now synchronized with Azure AD. You can continue to connect your Azure application with your on-premises credential.