Products and Features
- Getting Started with CloudRaya Container Registry
- How to use Sudo on a CloudRaya Linux VM
- Keeping Your CloudRaya Linux VMs Up-to-Date
- Maximizing StorageRaya with Essential Practices
- Assign Multiple IP Addresses to Virtual Machine
- Generating a CloudRaya API key
- Simplify CloudRaya Management with API
- Deploying a Virtual Machine on CloudRaya
- Deploying a Kubernetes Cluster on KubeRaya
- Using StorageRaya – CloudRaya S3 Object Storage
- Opening Ping Access on Cloud Raya VM Public IP
- Maximize Your Storage Raya Access Speed with Content Delivery Network (CDN)
- How to Create Project Tag in Cloud Raya for More Organized VM Billing Report
- Exporting Cloud Raya VM to outer Cloud Raya's Infrastructure using Acronis Cyber Protect
- SSO Management on Cloud Raya
- Easy Steps to Enable VPC in Cloud Raya
- Using the SSH key Feature in Cloud Raya Dashboard
- Cloud Raya Load Balancer, Solution to Distribute Load Equally
- Create your own VPN server with DNS-Level AdBlocker using PiVPN
- Fix Broken LetsEncrypt SSL Certificate due to Expired Root CA Certificate
- How to Make a Snapshot and Configure VM Backup in Cloud Raya
- How to Request Services or Licenses Products
- Adding, Attaching, and Resize Root Storage Disk in Cloud Raya VPS
- Managing your DNS Zone with DNS Bucket in Cloud Raya
- Create VM, Custom Package, Reinstall VM, and Adjusting Security Profile
- How to backup Linux VM via Acronis in Cloud Raya
- How to Backup Desktop Linux and Windows via Acronis in Cloud Raya
- Backing-Up Cloud Raya Windows VM Using Acronis Cyber Protect
- Load Balancing in Cloud Raya
- Establishing a VPN in Cloud Raya
- Generating an API Token
- Deploying a Virtual Machine in Cloud Raya
- Show Remaining Articles ( 17 ) Collapse Articles
- How to backup Linux VM via Acronis in Cloud Raya
- How to Backup Desktop Linux and Windows via Acronis in Cloud Raya
- Maximizing StorageRaya with Essential Practices
- Using StorageRaya – CloudRaya S3 Object Storage
- Building a Static Website Using Storage Raya S3 Bucket
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Maximize Your Storage Raya Access Speed with Content Delivery Network (CDN)
- Managing Storage Raya from various tools and from various OS
- Binding NextCloud with CloudRaya S3 Object Storage as External Storage Mount
- How to use Sudo on a CloudRaya Linux VM
- Keeping Your CloudRaya Linux VMs Up-to-Date
- Implement Multi-Factor Authentication on CloudRaya Linux VM
- Assign Multiple IP Addresses to Virtual Machine
- Deploying a Virtual Machine on CloudRaya
- Configurating cPanel Using Ubuntu 20.04 on CloudRaya – Part 2
- Deploying cPanel Using Ubuntu 20.04 on CloudRaya - Part 1
- Exporting Cloud Raya VM to outer Cloud Raya's Infrastructure using Acronis Cyber Protect
- Using the SSH key Feature in Cloud Raya Dashboard
- Adding, Attaching, and Resize Root Storage Disk in Cloud Raya VPS
- Create VM, Custom Package, Reinstall VM, and Adjusting Security Profile
- How to backup Linux VM via Acronis in Cloud Raya
- Backing-Up Cloud Raya Windows VM Using Acronis Cyber Protect
- Deploying a Virtual Machine in Cloud Raya
Integration
- Implement Multi-Factor Authentication on CloudRaya Linux VM
- Accessing KubeRaya Cluster Using the Kubernetes Dashboard
- Building a Static Website Using Storage Raya S3 Bucket
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Integrating Strapi Content to Frontend React - Part 3
- Content Management with Strapi Headless CMS - Part 2
- Strapi Headless CMS Installation in CloudRaya - Part. 1
- Using SSH Key on CloudRaya VM with PuTTY
- Installing Multiple PHP Versions in One VM for More Flexible Web Development
- Replatforming Apps to K8s with RKE and GitLab CI
- OpenAI API Integration: Completions in PHP
- Building an Email Server on CloudRaya Using iRedMail
- Improving Email Delivery with Sendinblue SMTP Relay
- Building a Self Hosted Password Manager Using Passbolt
- How to Install Podman on Almalinux/Rocky Linux 9
- ElkarBackup: GUI Based backup Tools based on Rsync and Rsnapshot
- Improving Webserver Performance with SSL Termination on NGINX Load Balancer
- Using NGINX as an HTTP Load Balancer
- Automating Task with Cronjob
- Upgrade Zimbra and the OS Version
- Deploy Mailu on Rancher Kubernetes
- Export and Import Database in MySQL or MariaDB Using Mysqldump
- Backup & Sync Local and Remote Directories Using RSYNC
- Managing Storage Raya from various tools and from various OS
- Binding NextCloud with CloudRaya S3 Object Storage as External Storage Mount
- Simple monitoring and alerting with Monit on Ubuntu 22.04 LTS
- VS Code on your browser! How to install code-server on a VM
- Implementing Redis HA and Auto-Failover on Cloud Raya
- Using XFCE Desktop Environment on Cloud Raya VM
- Installing Python 3.7-3.9 on Ubuntu 22.04 Jammy LTS using PPA
- Implementing Continuous Integration with Gitlab CI and Continuous Delivery with Rancher Fleet
- Using Collabora Online on Cloud Raya NextCloud's VM
- Installing NextCloud in Cloud Raya- Detail Steps from the Beginning to the Very End
- Set Up High Availability PostgreSQL Cluster Using Patroni on Cloud Raya
- Set Up WAF KEMP in Cloud Raya Part 2
- Set Up WAF KEMP in Cloud Raya Part 1
- Using the SSH key Feature in Cloud Raya Dashboard
- Monitor Your Services Uptime Using Uptime Kuma
- Hosting Static Website with Hugo on Cloud Raya
- Kubernetes Ingress Controller using SSL in CloudRaya
- Reverse Proxy management using Nginx Proxy Manager
- Create your own VPN server with DNS-Level AdBlocker using PiVPN
- How to deploy Portainer on Linux to easily manage your docker containers
- High Availability Kubernetes Using RKE in Cloud Raya Part 3
- High Availability Kubernetes Using RKE in Cloud Raya Part 2
- High Availability Kubernetes Using RKE in Cloud Raya Part 1
- How to backup Linux VM via Acronis in Cloud Raya
- How to Backup Desktop Linux and Windows via Acronis in Cloud Raya
- Deploying Magento on Cloud Raya
- How to Install Nextcloud on Cloud Raya
- How to Install CWP in Cloud Raya
- How to Install Node.js and Launch Your First Node App
- How to install and secure MariaDB on Ubuntu 18.04 and 20.04 on Cloud Raya
- How to Install and Securing MongoDB on Ubuntu 18.04 and 20.04
- Classes: Post Installation on Ansible
- Classes: Install and Configure Ansible
- Classes: Introduction to Ansible for a robust Configuration Management
- How to Setup Active Directory Domain Service & DNS with Cloud Raya
- How to Host Your Own Docker Hub in Cloud Raya
- How to Setup Your Own Laravel with Nginx in Ubuntu 18.04
- How to Deploy Container in Cloud Raya using Docker
- Securing CentOS with iptables
- Install and Configure Squid Proxy in Ubuntu
- Installing Apache and Tomcat: A Quick Way
- Securing Ubuntu with UFW
- Install a Node.js and Launch a Node App on Ubuntu 18.04
- Installing LAMP in Ubuntu
- Installing LEMP Stack on Ubuntu 18.04
- Show Remaining Articles ( 53 ) Collapse Articles
- Articles coming soon
- Implement Multi-Factor Authentication on CloudRaya Linux VM
- Configurating cPanel Using Ubuntu 20.04 on CloudRaya – Part 2
- Deploying cPanel Using Ubuntu 20.04 on CloudRaya - Part 1
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Integrating Strapi Content to Frontend React - Part 3
- Content Management with Strapi Headless CMS - Part 2
- Strapi Headless CMS Installation in CloudRaya - Part. 1
- Using SSH Key on CloudRaya VM with PuTTY
- Building an Email Server on CloudRaya Using iRedMail
- Improving Email Delivery with Sendinblue SMTP Relay
- Building a Self Hosted Password Manager Using Passbolt
- ElkarBackup: GUI Based backup Tools based on Rsync and Rsnapshot
- Improving Webserver Performance with SSL Termination on NGINX Load Balancer
- Using NGINX as an HTTP Load Balancer
- Upgrade Zimbra and the OS Version
- Deploy Mailu on Rancher Kubernetes
- Managing Storage Raya from various tools and from various OS
- Binding NextCloud with CloudRaya S3 Object Storage as External Storage Mount
- Simple monitoring and alerting with Monit on Ubuntu 22.04 LTS
- VS Code on your browser! How to install code-server on a VM
- Implementing Redis HA and Auto-Failover on Cloud Raya
- Using XFCE Desktop Environment on Cloud Raya VM
- Implementing Continuous Integration with Gitlab CI and Continuous Delivery with Rancher Fleet
- Using Collabora Online on Cloud Raya NextCloud's VM
- Installing NextCloud in Cloud Raya- Detail Steps from the Beginning to the Very End
- Set Up WAF KEMP in Cloud Raya Part 2
- Set Up WAF KEMP in Cloud Raya Part 1
- Monitor Your Services Uptime Using Uptime Kuma
- Create your own VPN server with DNS-Level AdBlocker using PiVPN
- How to deploy Portainer on Linux to easily manage your docker containers
- High Availability Kubernetes Using RKE in Cloud Raya Part 3
- High Availability Kubernetes Using RKE in Cloud Raya Part 2
- High Availability Kubernetes Using RKE in Cloud Raya Part 1
- How to Install Nextcloud on Cloud Raya
- Classes: Post Installation on Ansible
- Classes: Install and Configure Ansible
- Classes: Introduction to Ansible for a robust Configuration Management
- Connect Windows Active Directory on Cloud Raya with Azure AD
- How to Host Your Own Docker Hub in Cloud Raya
- How to Deploy Container in Cloud Raya using Docker
- Show Remaining Articles ( 25 ) Collapse Articles
- Accessing KubeRaya Cluster Using the Kubernetes Dashboard
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Integrating Strapi Content to Frontend React - Part 3
- Content Management with Strapi Headless CMS - Part 2
- Strapi Headless CMS Installation in CloudRaya - Part. 1
- Creating Interactive Chatbot with OpenAI API in PHP
- Installing Multiple PHP Versions in One VM for More Flexible Web Development
- OpenAI API Integration: Completions in PHP
- Improving Webserver Performance with SSL Termination on NGINX Load Balancer
- Using NGINX as an HTTP Load Balancer
- Automating Task with Cronjob
- How to Deploy Django App on Cloud Raya VM Using Gunicorn, Supervisor, and Nginx
- How to Install Node.js and Launch Your First Node App
- How to Setup Your Own Laravel with Nginx in Ubuntu 18.04
- Install a Node.js and Launch a Node App on Ubuntu 18.04
- How to use Sudo on a CloudRaya Linux VM
- Keeping Your CloudRaya Linux VMs Up-to-Date
- Implement Multi-Factor Authentication on CloudRaya Linux VM
- Using SSH Key on CloudRaya VM with PuTTY
- Building a Self Hosted Password Manager Using Passbolt
- Improving Webserver Performance with SSL Termination on NGINX Load Balancer
- Export and Import Database in MySQL or MariaDB Using Mysqldump
- Backup & Sync Local and Remote Directories Using RSYNC
- How to Deploy Django App on Cloud Raya VM Using Gunicorn, Supervisor, and Nginx
- Set Up WAF KEMP in Cloud Raya Part 2
- Set Up WAF KEMP in Cloud Raya Part 1
- Using the SSH key Feature in Cloud Raya Dashboard
- How to backup Linux VM via Acronis in Cloud Raya
- How to Backup Desktop Linux and Windows via Acronis in Cloud Raya
- Securing CentOS with iptables
- Securing Ubuntu with UFW
- Show Remaining Articles ( 1 ) Collapse Articles
- Configurating cPanel Using Ubuntu 20.04 on CloudRaya – Part 2
- Deploying cPanel Using Ubuntu 20.04 on CloudRaya - Part 1
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Integrating Strapi Content to Frontend React - Part 3
- Content Management with Strapi Headless CMS - Part 2
- Strapi Headless CMS Installation in CloudRaya - Part. 1
- Creating Interactive Chatbot with OpenAI API in PHP
- Installing Multiple PHP Versions in One VM for More Flexible Web Development
- Building an Email Server on CloudRaya Using iRedMail
- Building a Self Hosted Password Manager Using Passbolt
- Improving Webserver Performance with SSL Termination on NGINX Load Balancer
- Using NGINX as an HTTP Load Balancer
- Installing Python 3.7-3.9 on Ubuntu 22.04 Jammy LTS using PPA
- Reverse Proxy management using Nginx Proxy Manager
- Install and Configure Squid Proxy in Ubuntu
- Installing Apache and Tomcat: A Quick Way
- Installing LAMP in Ubuntu
- Installing LEMP Stack on Ubuntu 18.04
- Show Remaining Articles ( 3 ) Collapse Articles
- Building a Static Website Using Storage Raya S3 Bucket
- Integrating S3 Storage Raya and Strapi for Asset Storage Optimization – Part 4
- Integrating Strapi Content to Frontend React - Part 3
- Content Management with Strapi Headless CMS - Part 2
- Strapi Headless CMS Installation in CloudRaya - Part. 1
- Creating Interactive Chatbot with OpenAI API in PHP
- Installing Multiple PHP Versions in One VM for More Flexible Web Development
- OpenAI API Integration: Completions in PHP
- Hosting Static Website with Hugo on Cloud Raya
- Deploying Magento on Cloud Raya
- How to Install CWP in Cloud Raya
- How to Setup Active Directory Domain Service & DNS with Cloud Raya
- Articles coming soon
Building an Email Server on CloudRaya Using iRedMail
In the previous tutorial, we have learned on how SMTP relay can increase email delivery. Today, we will show you how to create an email server in CloudRaya using iRedMail, as this configuration allows you to have full access to your email infrastructure.
About iRedMail
iRedMail is an open-source platform based on a Linux/BSD server. The great advantage of iRedMail is its shell script, which allows users to automatically install and configure the entire components needed for an email server. iRedMail also provides mission-critical features needed to operate an email server such as antispam, antivirus, and user management tools. Last but not least, it allows us to infinitely create mailboxes and mail domains that can be stored in database systems such as MariaDB/MySQL, PostgreSQL, or OpenLDAP.
Other than the free open-source version, iRedMail also has paid versions which are iRedMail Easy and iRedMail Pro.
Pre-Instalation
▶️ System Requirement
There are several requirement we need to fulfill before installing iRedMail in Debian or Linux Ubuntu, which are as follows:
- It is highly recommended to use a vanilla server (vanilla as in no component such as MySQL, Postfix, Dovecot, etc. installed in the server), as iRedMail will automatically install all the necessary components in the installation process.
- CloudRaya recommends a VM with at least 4 GB of RAM. This size of VM can already accommodate low-traffic email server with antispam/antivirus protection enabled.
- Make sure the following UID/GID is not used by other users/groups: 2000, 2001, and 2002.
grep -E "^user[0-9]*:.*:(2000|2001|2002):" /etc/passwdgrep -E "^group[0-9]*:.*:(2000|2001|2002):" /etc/group
- Make sure the following UID/GID is not used by other users/groups: 2000, 2001, and 2002.
- Make sure you have the following ports open. You can open the ports in the Access Control List configuration at CloudRaya VPC. You can read more about how to open a port in CloudRaya VPC here.
▶️ Set FQDN as CloudRaya VM hostname

We will use an Ubuntu server in this tutorial.
First, we need to change the hostname of our VM. The hostname will be used by iRedMail as a link to access our web panel. Use the standard FQDN (Fully Qualified Domain Name) with the following as an example:
# hostnamectl hostname mail3.cloudforindonesia.com
Next, update the static table lookup file of the hostname with the following at directory /etc/hosts.
# nano /etc/hosts
Add our hostname in the following line:
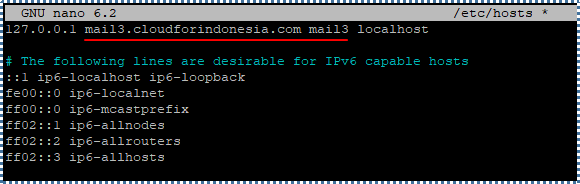
Reboot VM to apply the changes
# reboot
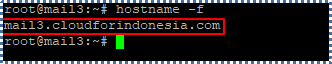
To check does the changes have been applied or not, use the following:
# hostname -f
iRedMail Installation
Install the following packages needed for iRedMail installer:
# sudo apt-get install gzip dialog
▶️ Download the Latest iRedMail Version
Download the latest iRedMail version using the following command wget
# wget https://github.com/iredmail/iRedMail/archive/refs/tags/1.6.2.tar.gz
Exctract the .tar archive:
# cd /root/
# tar zxf 1.6.2.tar.gz
Open the extracted folder with the following command:
# cd iRedMail-1.6.2/
▶️ Run iRedMail Installer
Run installer .sh within the folder with bash
# bash iRedMail.sh

You can configure your email server through several pop-up dialogues that appear throughout the installation process.
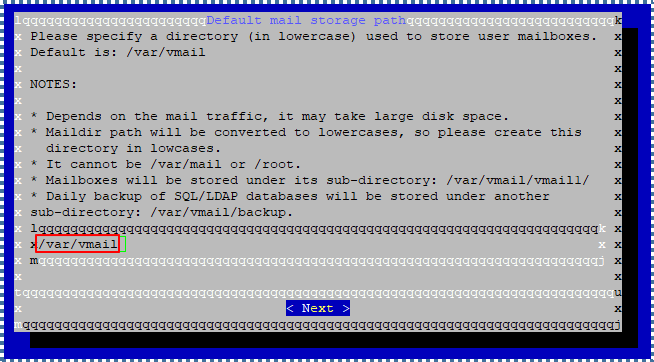
Choose your storage location. The default location is /var/vmail/.
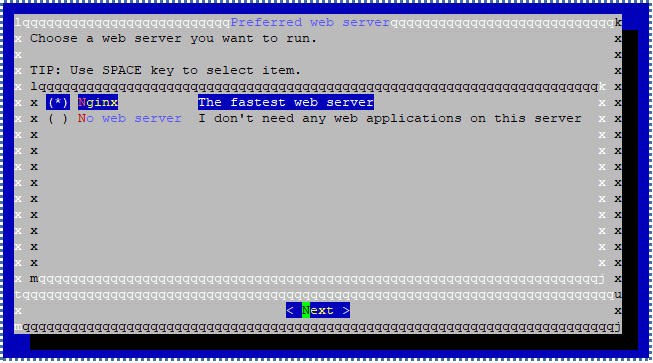
Next, choose what web server will be used for iRedMail. This tutorial will choose NGINX as the web server.
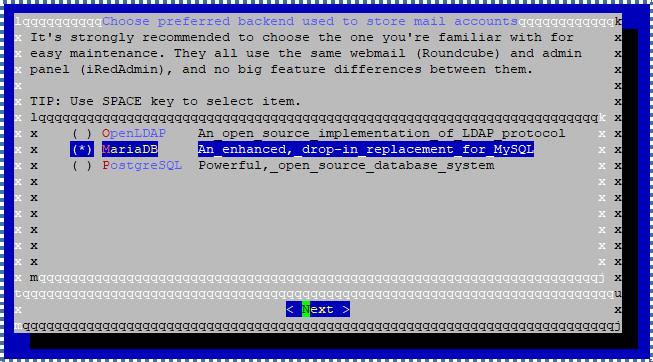
Decide which database system to store the email account. We recommend you choose the system you are familiar with. This tutorial will choose MariaDB as the database system.
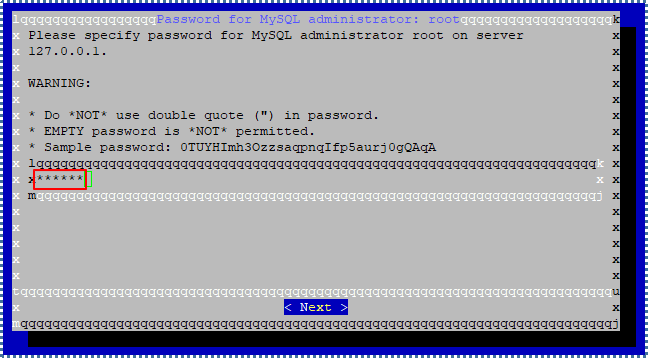
Create password for your MySQL root.
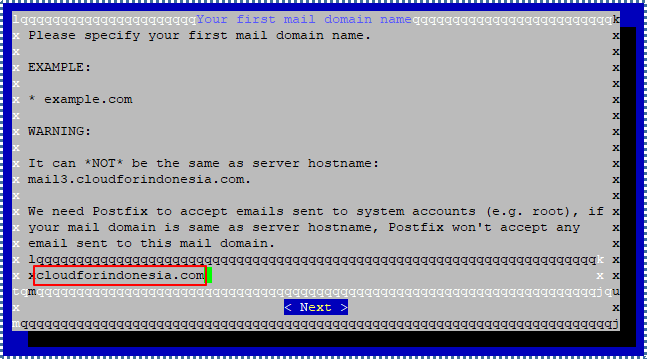
In the next pop-up, you will be asked to input the desired domain name. To add more email domain, you can do it in iRedMail admin panel.
Make sure to not use the same domain as the VM hostname domain.
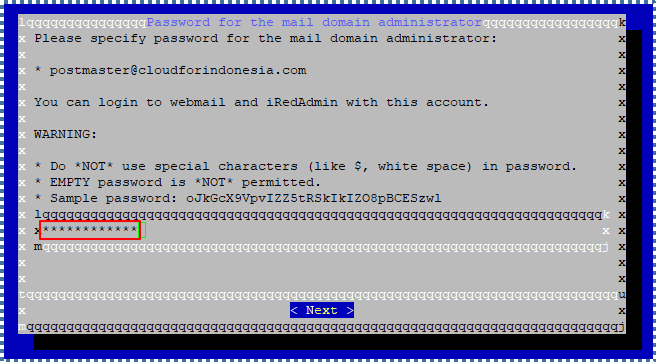
Next, create a password for the administrator domain email.

You will be given several optional components in the next pop-up. We recommend you install all of them.
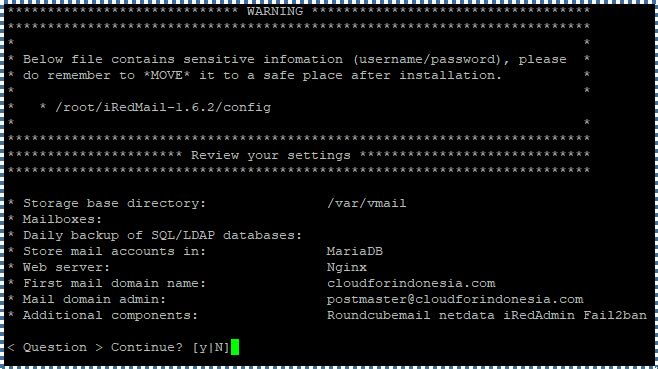
Your final configuration will be shown to you. To install all of the server mail components as configured, type Y
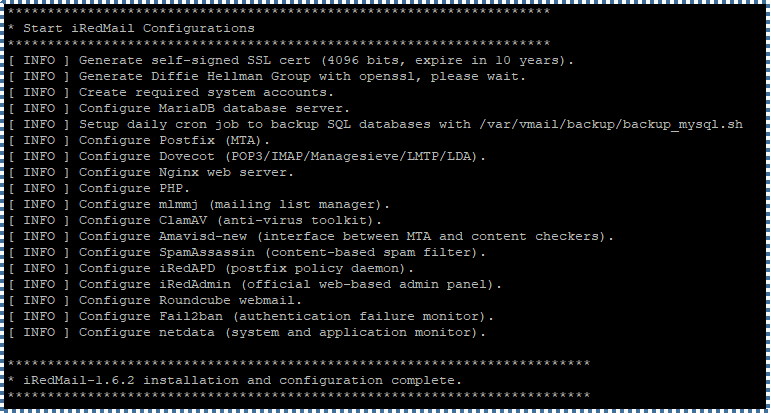
The installation process will take time. If complete, you will be shown the list of installed components by iRedMail wizard.

The last step of the process is to decide whether or not you want to activate the firewall rules provided by iRedMail. To activate it, type Y.
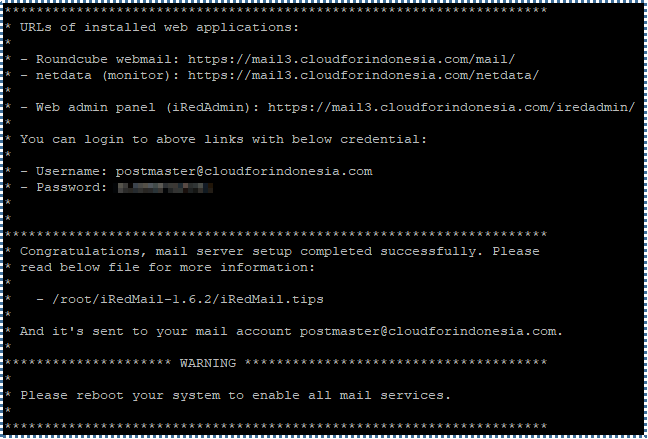
iRedMail installation is complete. Several important pieces of information will be shown to you, such as the URL for webmail, the URL to monitor the server through netdata, and the URL for the iRedAdmin panel with the login credential. You can find detailed information about the iRedMail through iRedmail.tips file.
# reboot
Reboot the VM to apply the installation with the command above.
Post-Installation
▶️ Add MX Record
Now, we need to add an MX record to our DNS management panel to register the domain we use to be recognized as a mail exchange.
The function of the MX record is to choose which server is responsible for sending and receiving emails for our domain. MX record installation to our server ensures our email delivery.
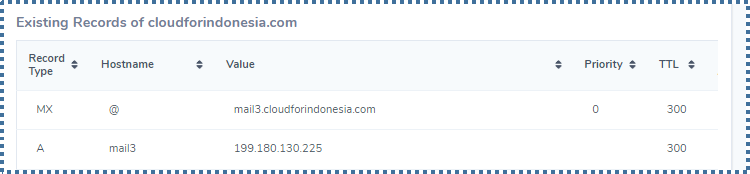
Create A and MX records as new records in the DNS management panel and wait for the propagation to finish (can be up to 48 hours).
▶️ Let’s Encrypt TLS Certificate Installation

A ‘not secure’ message will appear if you attempt to access the web panel. It happens due to the self-signed TLS certificate iRedMail uses. To avoid the message, you can install TLS from Let’s Encrypt for free.
⏭️ Obtain the Certificate
Access the VM through SSH, then run the following command to install certbot and its plug-in for NGINX at the Ubuntu repository.
# apt install certbot python3-certbot-nginx -y
Let’s use the webroot plugin to obtain the certificate since iRedMail has configured the TLS in the NGINX virtual host as default.
# sudo certbot certonly -a webroot --agree-tos --email tiyan@cloudforindonesia.com -d mail3.cloudforindonesia.com -w /var/www/html/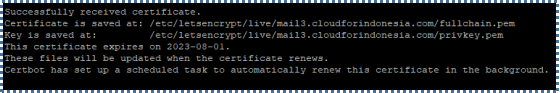
The above message will appear if every step is performed correctly. In this tutorial, all certificates and their components are stored at
/etc/letsencrypt/live/mail3.cloudforindonesia.com/.
⏭️ Installing the Certificate in NGINX
Now, we have to configure the NGINX web server to be able to use the new TLS certificate. First, let’s edit the SSL template file.
# sudo nano /etc/nginx/templates/ssl.tmpl
In the last 2 lines, you will find the following information:
…
ssl_certificate /etc/ssl/certs/iRedMail.crt;
ssl_certificate_key /etc/ssl/private/iRedMail.key;
In this tutorial, we will change it to:
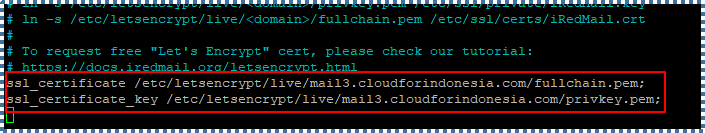
…
ssl_certificate /etc/letsencrypt/live/mail3.cloudforindonesia.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/mail3.cloudforindonesia.com/privkey.pem;
Save and close. Test the NGINX configuration and don’t forget to reload it with the following command.
# sudo nginx -t
# sudo systemctl reload nginx
At this point, when you open the admin page, you should not receive the ‘not secure’ message screen since the web server already uses the new TLS certificate.
⏭️ How to Install the Certificate in Postfix and Dovecot
You cannot just secure your web server with a TLS certificate. You also need to configure the Postfix SMTP and Dovecot IMAP server. It is important to configure these servers to avoid false warnings from mail client desktops, such as Outlook and Thunderbird, that the email is not equipped with a TLS certificate.
First, let’s edit the Postfix configuration:
# sudo nano /etc/postfix/main.cf
Find these 3 lines:
…
smtpd_tls_key_file = /etc/ssl/private/iRedMail.key
smtpd_tls_cert_file = /etc/ssl/certs/iRedMail.crt
smtpd_tls_CAfile = /etc/ssl/certs/iRedMail.crt
…
In this tutorial, we will change it into:
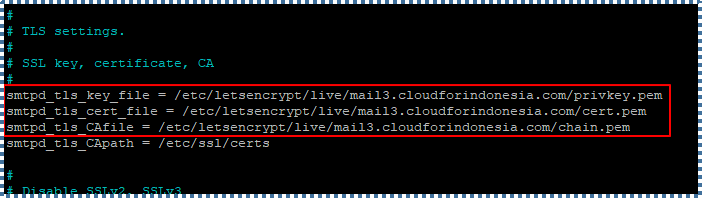
…
smtpd_tls_key_file = /etc/letsencrypt/live/mail3.cloudforindonesia.com/privkey.pem
smtpd_tls_cert_file = /etc/letsencrypt/live/mail3.cloudforindonesia.com/cert.pem
smtpd_tls_CAfile = /etc/letsencrypt/live/mail3.cloudforindonesia.com/chain.pem
…
Save and close, followed with reload-ing the configuration:
# sudo systemctl reload postfix
Next, we edit the configuration file for Dovecot:
# sudo nano /etc/dovecot/dovecot.conf
Find these 2 lines:
…
ssl_cert = </etc/ssl/certs/iRedMail.crt
ssl_key = </etc/ssl/private/iRedMail.key
…
And change it into:
…
ssl_cert = </etc/letsencrypt/live/mail3.cloudforindonesia.com/fullchain.pem
ssl_key = </etc/letsencrypt/live/mail3.cloudforindonesia.com/privkey.pem
…
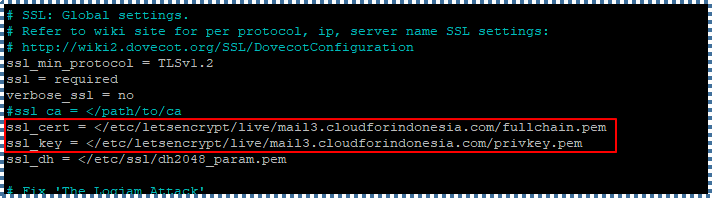
Save and close, followed with reload-ing the configuration:
# sudo systemctl reload dovecot
▶️ Increasing Email Delivery Rate
SPF, DKIM, and DMARC work together to ensure that any emails you receive come from legitimate sources and are not being tampered with in transit, reducing the risk of phishing and spoofing.
⏭️ SPF record
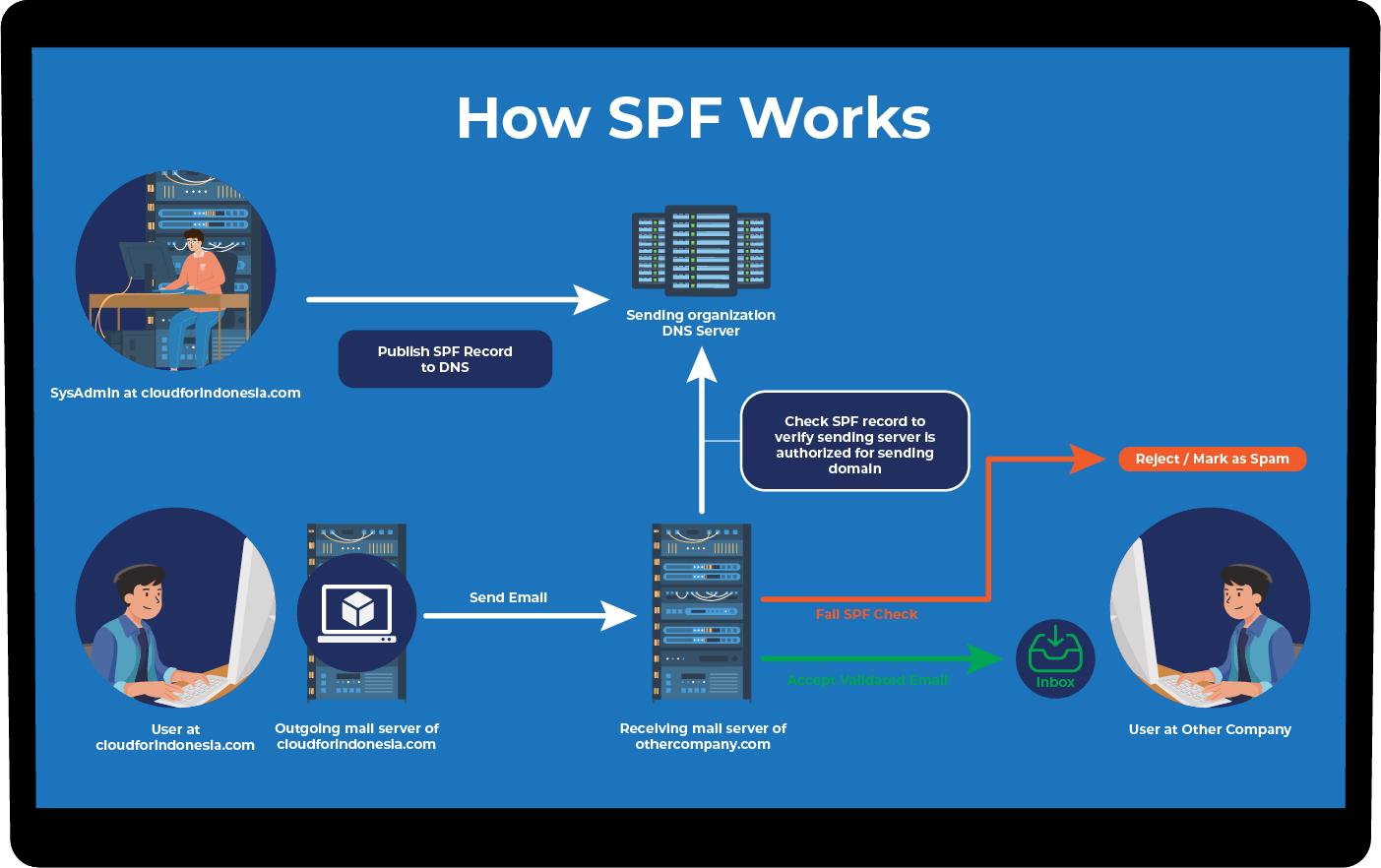
SPF (Sender Policy Framework) is a DNS record that contains list hosts or IP addresses allowed to send email on behalf of our domain, effectively validating the email and preventing it from being falsified. Within the record is also an additional configuration regulating what will happen if the email is sent not following the proper configuration.
Create a new TXT record at the DNS management panel. In this tutorial, we will create the record as follow:
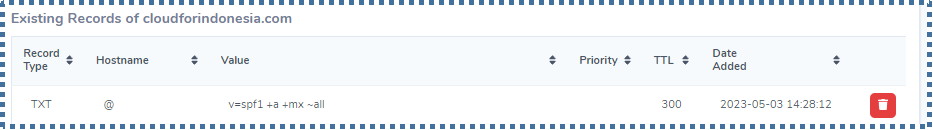
The point of the above configuration is to allow any IP addresses tied to the domain to sent emails and to send it from server registered in MX record, with ~all mark as a soft fail.
⏭️ DKIM record
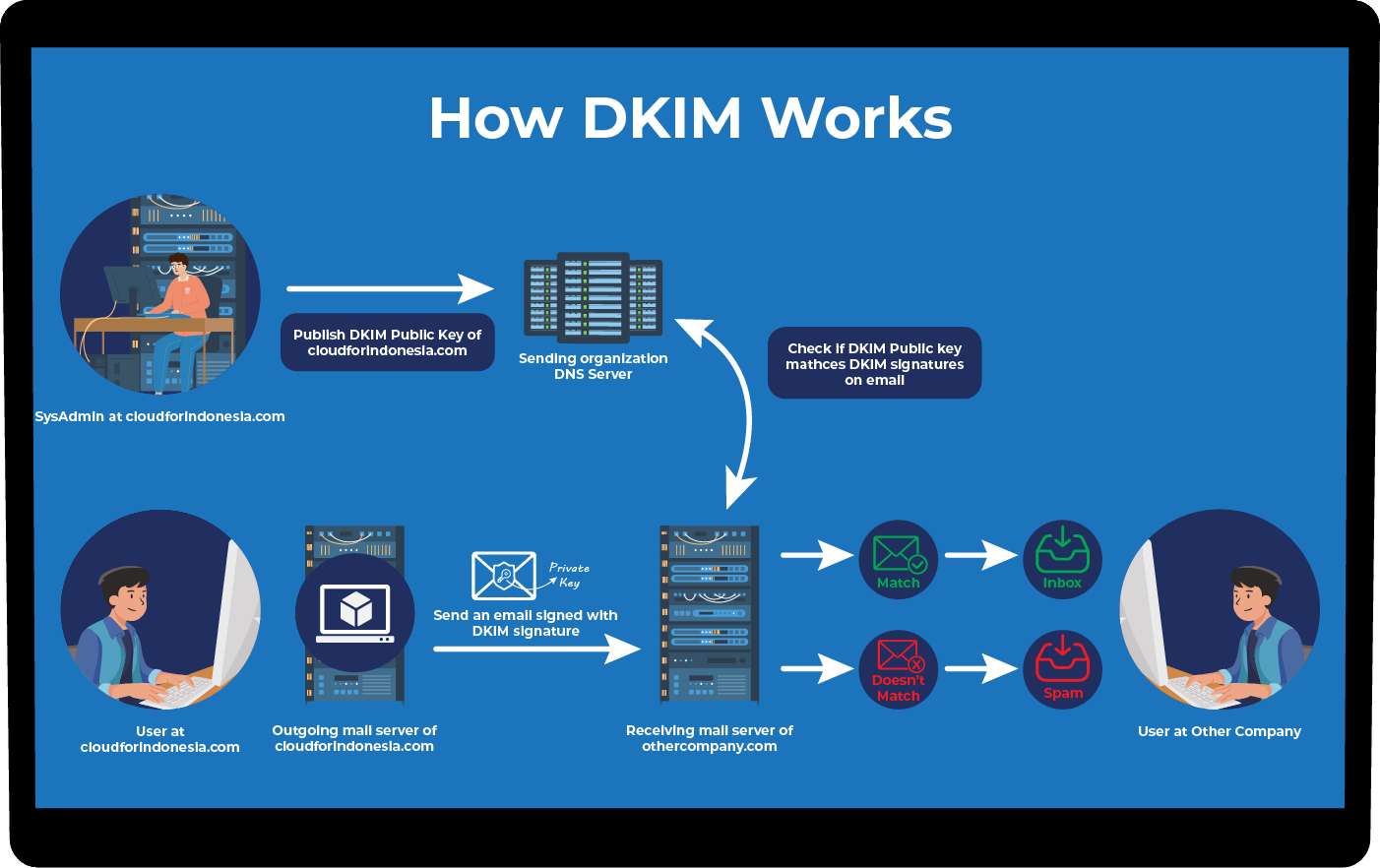
DKIM (DomainKeys Identified Mail) is the technology used to verify the legitimacy of the email received comes from the sender domain. It works by encrypting a private key to the email sent, which is then saved as a public key into our DNS record domain.
When the email is received, the receiver server will perform DKIM verification using the public key stored in the DNS record. Successful verification means the email is legitimate and there is no tampering or change during transit.
iRedMail installation has automatically configured the DKIM private key into our email server during the installation process. What you only need to do is to add the DKIM public key to the DNS management.
Run the following command to display the DKIM public key:
# sudo amavisd-new showkeys
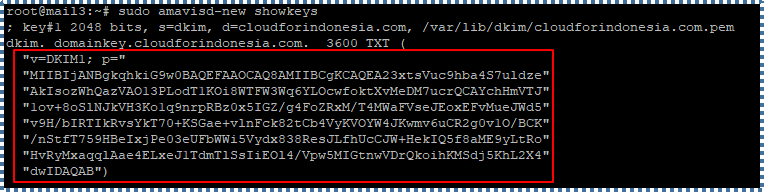
Create a new TXT record in the DNS management panel based on the public key displayed. Make sure to delete all quotation marks and spacing as displayed below.

Check the DKIM record using the following command.
# sudo amavisd-new testkeys
The process may take some time depending on the propagation process. If the propagation is finished and the DKIM record you input is correct, you will see the pass as follows.

⏭️ DMARC record
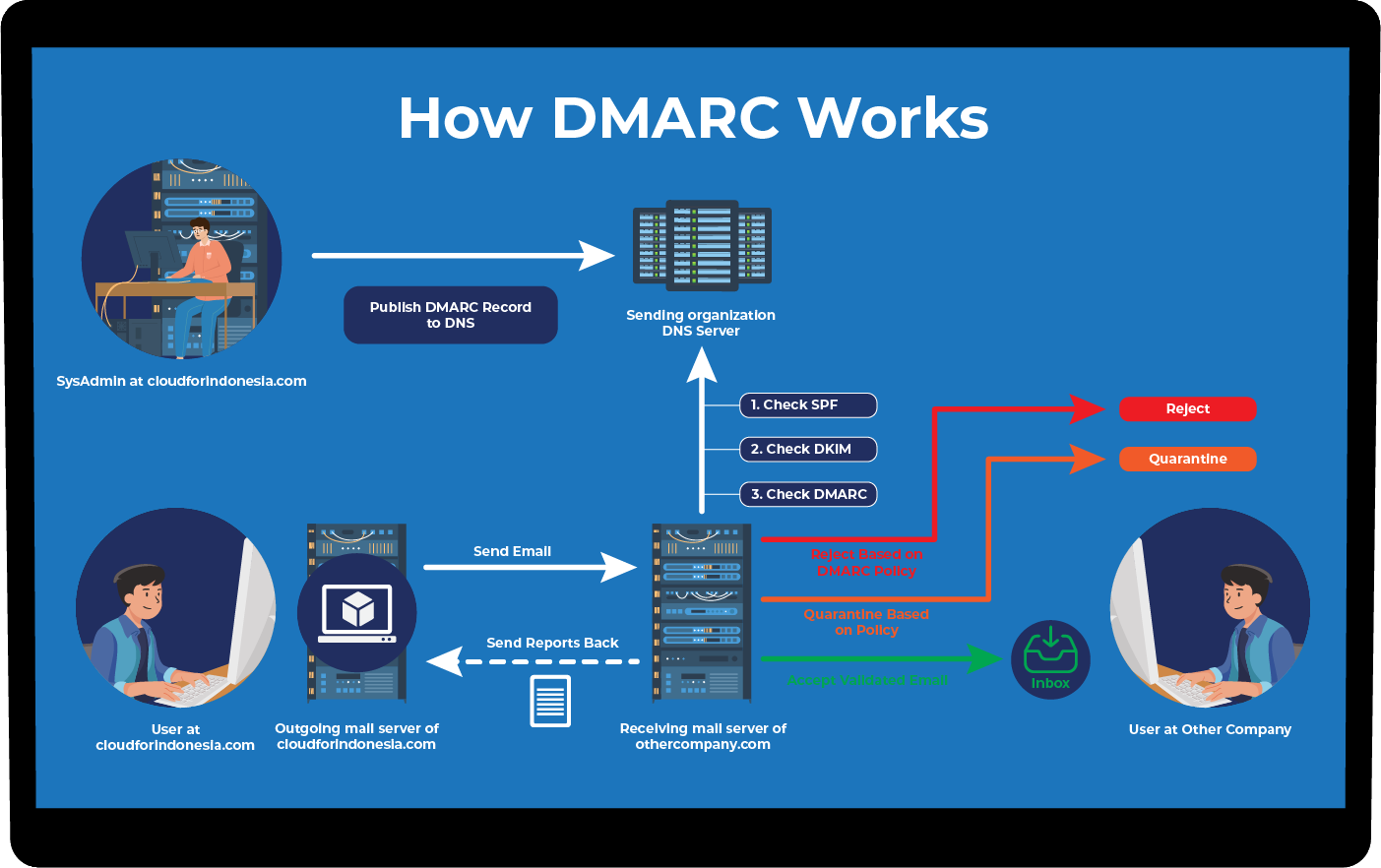
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is an email verification protocol that regulates how to handle received emails that fail to be verified by either SPF or DKIM.
DMARC allows email receivers to create a regulation on what to do if the email received fails to be verified, such as rejecting the email or quarantining the email in the spam folder. DMARC also allows the sender to receive a report about the status of the sent email, thus increasing the security of the email.
To add DMARC, create a new TXT record filled with common DMARC configuration as follow.
v=DMARC1; p=none; rua=mailto:report@cloudforindonesia.com
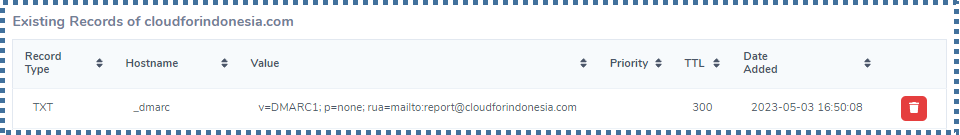
The above example will activate the “none” policy for our domain. This policy will make the receiver server send reports to report@your-domain.com if there are any emails that fail SPF or DKIM verification without giving special instructions on how to handle the failed-to-verified emails.
By choosing the “none” policy, we can collect the report and analyze emails sent from our domain. Thus, we can quickly find a rising problem and make sure emails from our domains can be verified by others. After a while, we can decide to tighten the policy into “quarantine” or “reject” if necessary.
Exploring and Using iRedMail
Now, we can start to explore iRedMail admin panel and start sending our first email.
▶️ Web Panel Access
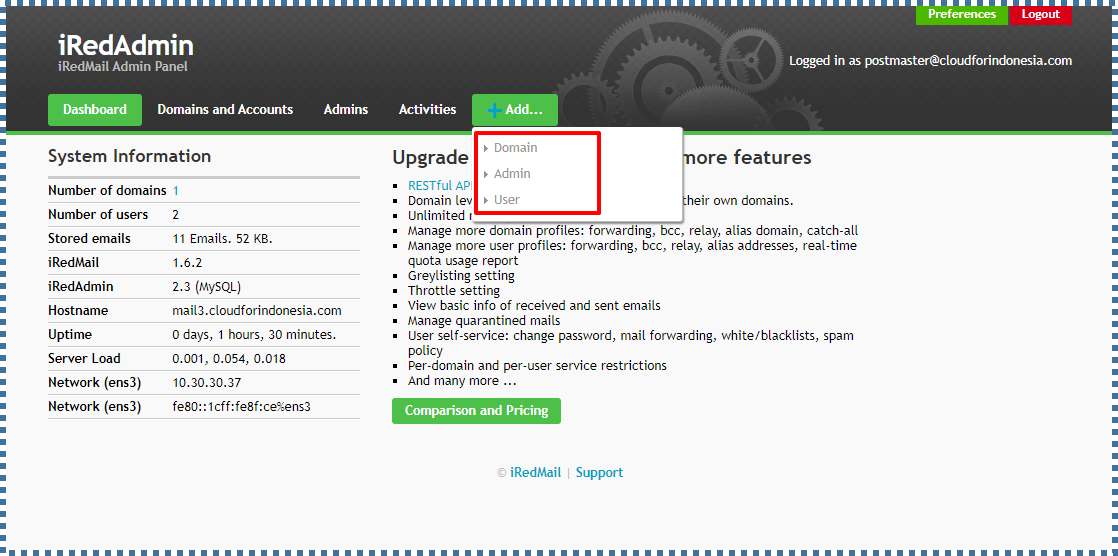
You can find several things that you can do within the panel, such as managing domain, account, etc.

Now, let’s add the email account we want to use to send our first email with.
Access the web mail of the account you previously created. You can find further example from the following page https://mail3.cloudforindonesia.com/mail/
Create and send your first email.
Check if the email you sent from the iRedMail is received to the designated receiver.
Conclusion
That is all from this tutorial of building iRedMail mail server in CloudRaya’s virtual infrastructure.
Don’t forget to check other knowledge base at CloudRaya Knowledge Base and visit our blog to learn the up-to-date news of the IT world. Perhaps you like to learn from a video instead? Then go to our YouTube channel, where you can find the video version of this tutorial and many others.